February 6, 2026
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Suspendisse varius enim in eros elementum tristique. Duis cursus, mi quis viverra ornare, eros dolor interdum nulla, ut commodo diam libero vitae erat. Aenean faucibus nibh et justo cursus id rutrum lorem imperdiet. Nunc ut sem vitae risus tristique posuere.
Real-world asset tokenization has moved decisively beyond pilot programs and controlled proofs of concept.
What began as experimentation by innovation teams is now being driven by core business units within banks, asset managers, fintech platforms, and market infrastructure providers. This shift has created demand for white-label RWA tokenization platforms that can be deployed repeatedly, operated reliably, and governed responsibly.
White-label in this context refers to surface-level branding and to designing a real-world asset tokenization platform that can support different asset types, operate across jurisdictions, enforce issuer-specific rules, and enable repeatable launches without constant custom development. This is why global market infrastructure players are actively building tokenization rails.
To meet these expectations, platforms must be built with long-term operation in mind. That requires discipline in architecture, compliance, and governance from the very beginning.
In RWA tokenization, white-label means multiple issuers or operators running on a single shared platform while each experience it as their own isolated environment. This is fundamentally a multi-tenant systems challenge and a design exercise.
A white-label tokenization platform must support multiple issuers that may tokenize different asset classes, target different investor bases, and operate under different regulatory frameworks. These issuers share infrastructure while maintaining separate data, workflows, and operational visibility. Investor records, asset documents, transaction histories, and reporting outputs must be isolated by tenant, with no risk of cross-contamination.
Tenant isolation extends beyond databases. Wallet allowlists must be issuer-specific. Compliance decisions must apply only within the issuer's domain. Administrative actions and reporting views must respect tenant boundaries. When these constraints are enforced at the architectural level, issuers gain confidence that the platform can support real operations at scale.
A sustainable asset tokenization platform development strategy depends on clearly separating what issuers can configure from what must remain fixed in the core.
Issuers typically expect flexibility around branding, supported languages, investor onboarding flows, fee structures, and asset-specific rule parameters. These elements vary by business model and market and must be adjustable without code changes.
At the same time, certain components must remain fixed to preserve integrity. Identity verification, compliance enforcement, and token issuance logic should be set to maintain issuer discretion.
These controls ensure consistent behavior across the platform and protect both the platform operator and participating issuers. This balance allows a compliant tokenization platform to remain flexible while maintaining stability.
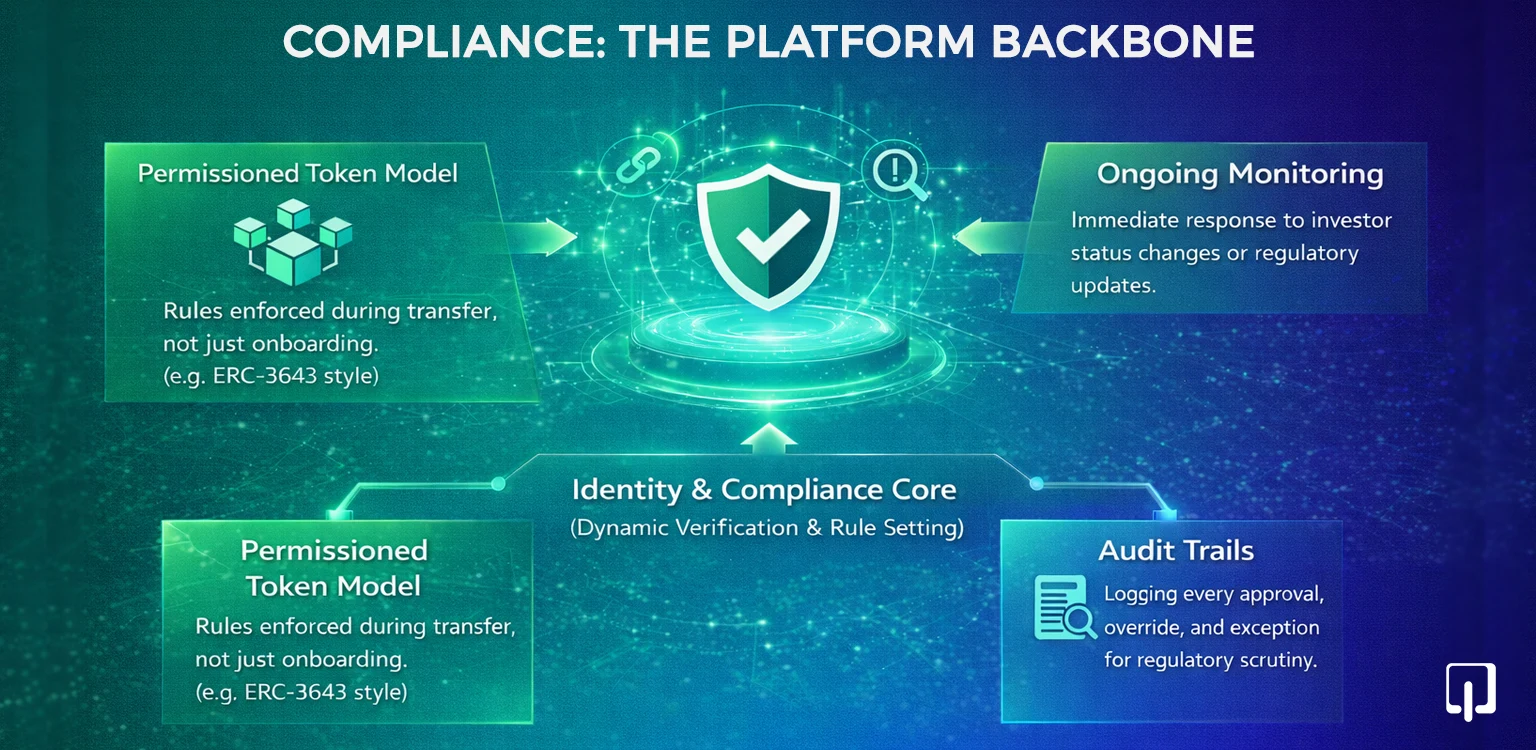
Real-world asset tokens often represent regulated products or legally binding economic interests. As a result, compliance obligations continue after investor onboarding and persist throughout the lifecycle of the asset, particularly during token transfers.
In many jurisdictions, transfer restrictions are mandatory. Rules governing who can hold a token, who can receive it, and under what conditions transfers must be blocked are legally enforceable requirements. These rules should rely on off-chain agreements and application-level checks.
This is why production platforms rely on permissioned token models. Permissioned tokens enforce compliance now of transfer, ensuring that transactions follow rules even if initiated outside the main application. For enterprise-grade tokenization platforms, this approach is essential to maintaining regulatory credibility.
While regulatory specifics vary, a real-world asset tokenization platform generally requires a consistent set of compliance capabilities to operate responsibly.
Eligibility rules must account for accreditation or qualification requirements where applicable. Jurisdictional constraints such as residency limits or offering restrictions must be enforced consistently.
Beyond onboarding, platforms must support ongoing monitoring. Investor status can change over time due to regulatory updates or risk reassessments. Every approval, override, and exception must be logged, creating a clear audit trail that can withstand regulatory scrutiny.
Regulators and global oversight bodies consistently emphasize investor protection, transparency, and market integrity. Platforms are expected to demonstrate control over issuance, circulation, and governance.
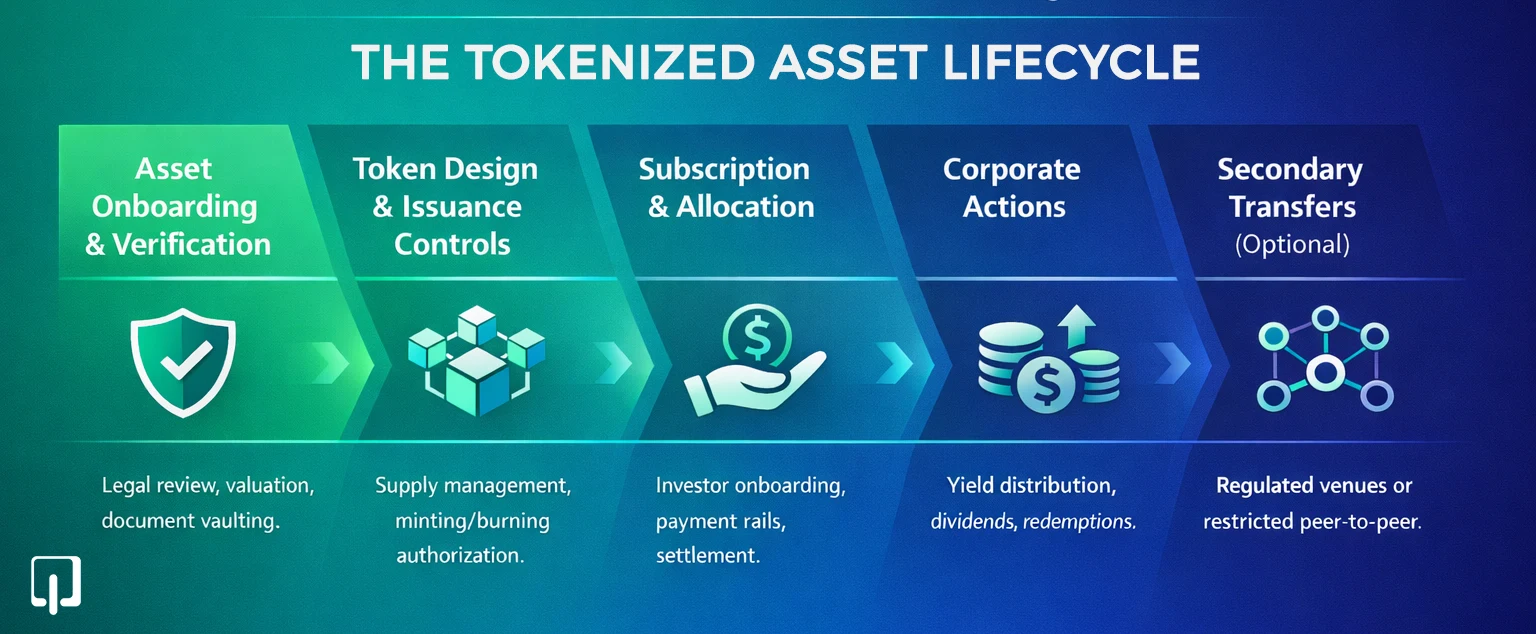
Tokenization begins long before tokens are issued. Asset onboarding establishes the legal and operational foundation for everything that follows. A serious real-world asset tokenization platform provides structured workflows for asset intake, verification, and approval.
Ownership proof, valuation methodology, legal structure, and supporting documentation must be reviewed and recorded. Document vaults and approval checkpoints ensure that decisions are traceable and defensible. This process protects issuers, investors, and platform operators alike.
Once an asset is approved, token design and issuance controls define how value is represented digitally. Supply management is a technical detail and a governance function.
Platforms must support minting and burning under explicit authorization, the ability to freeze or pause transfers when required, accurate cap table or allocation records, and issuer-level administrative actions. These controls ensure that token behavior remains aligned with the underlying asset's legal and economic structure.
Most tokenized assets are distributed through structured subscription flows in addition to open minting. Investors follow defined onboarding and subscription processes, after which allocations are finalized.
Payment rails may involve fiat, stablecoins, or a combination depending on jurisdiction and business model. Allocation rules and settlement events must be clearly recorded and auditable. Transparency at this stage is critical for investor trust and regulatory confidence.
Real assets evolve over time. A platform should support issuance and provide operational capability. Corporate actions such as yield distribution, dividends, redemptions, and buybacks are expected parts of asset management.
Secondary transfers are frequently requested, even in restricted form. Depending on jurisdiction, they may involve internal bulletin boards, integration with regulated venues, or restricted peer-to-peer models. A robust platform supports these variations while maintaining compliance and auditability.
In production environments, identity governs every meaningful action. Wallet addresses work alongside comprehensive systems. A compliant tokenization platform links identity verification directly to wallet registration, investor status changes, and transfer gating.
When an investor's eligibility changes, the platform must respond immediately. Transfers that were previously allowed may need to be blocked. This dynamic enforcement ensures that the platform remains compliant over time and at onboarding.
Many teams explore permissioned standards such as ERC-3643 because they are designed around regulated asset flows. These models emphasize permissioned transfers and built-in identity concepts.
The key insight is the standard itself and the architectural pattern. Successful tokenization platform architecture enforces rules at the token level while allowing off-chain systems to manage identity and policy configuration in a flexible manner.
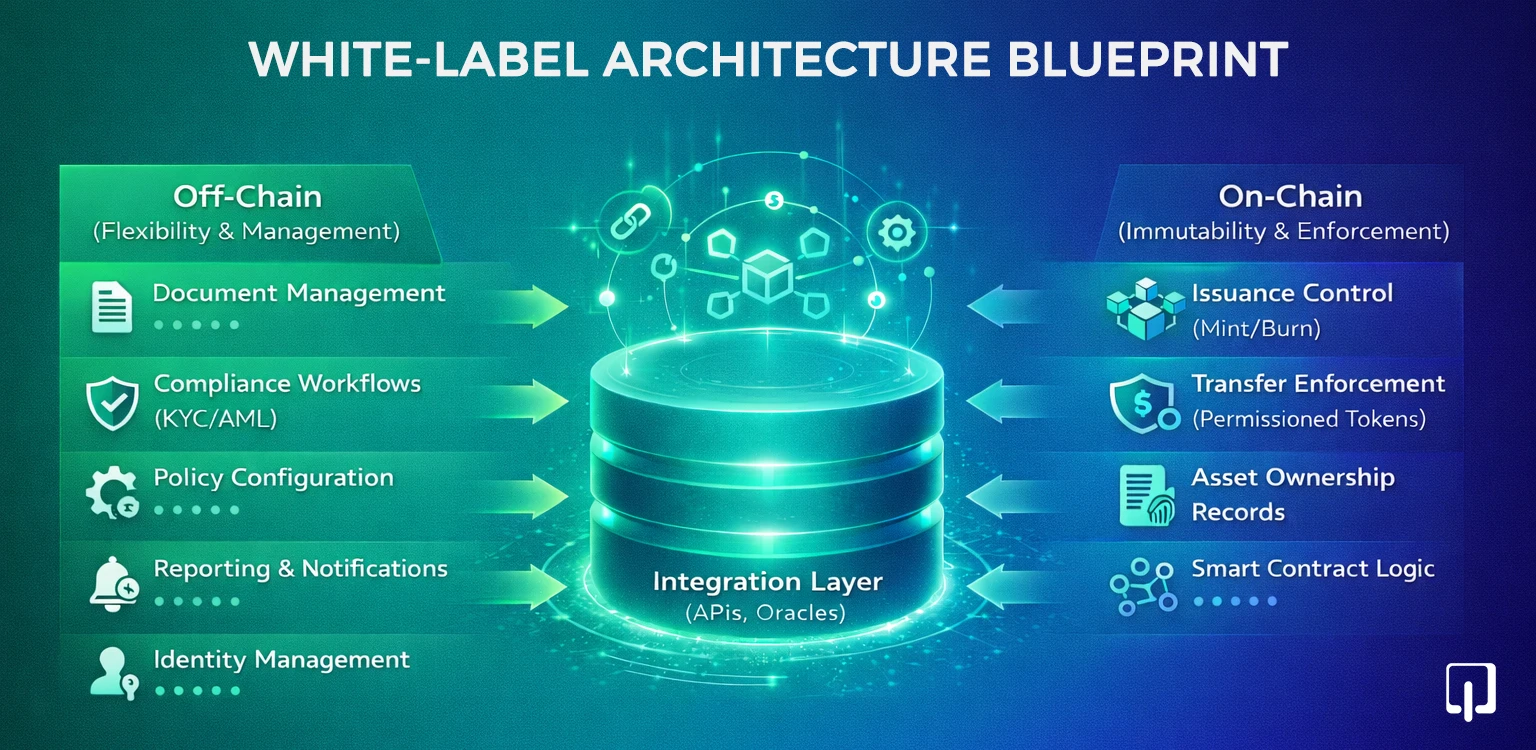
A scalable RWA tokenization architecture clearly separates on-chain and off-chain responsibilities. On-chain components focus on immutability, issuance control, and transfer enforcement. These elements benefit from blockchain's trust guarantees.
Off-chain systems handle document management, compliance workflows, policy configuration, reporting, and notifications. This separation allows platforms to adapt to regulatory change without constant contract redeployment.
Separate databases per tenant offer strong isolation but higher operational cost. Shared databases with strict partitioning offer efficiency and require rigorous access controls.
Similarly, token contracts may be deployed per issuer or shared with logical partitions. Each approach has trade-offs in cost, flexibility, and governance.
Operational reliability underpins trust. Monitoring, alerting, secure key management, custody integration, rate limiting, and multi-party approvals are baseline requirements for operating an enterprise-grade tokenization platform in real markets.
Successful white-label RWA tokenization platforms consistently include a set of core modules.
Issuer and admin consoles support asset creation, investor oversight, issuance controls, and reporting. Investor portals provide onboarding status, portfolio visibility, document access, and transfer requests where permitted. Compliance consoles manage review queues, risk flags, approvals, and regulatory reporting.
An integration layer connects the platform to KYC/AML providers, custodians or wallet services, payment rails, and external venues where applicable. These integrations often determine how quickly issuers can launch and scale.
Security planning begins with understanding realistic threats. Administrative misuse, smart contract vulnerabilities, data leakage between tenants, and identity spoofing or wallet takeover are common risk vectors.
Mitigating these risks requires layered controls. Role-based access control, action logging, secure key management, audited smart contracts with defined upgrade policies, and incident response planning are essential. Governance is as important as technical security.
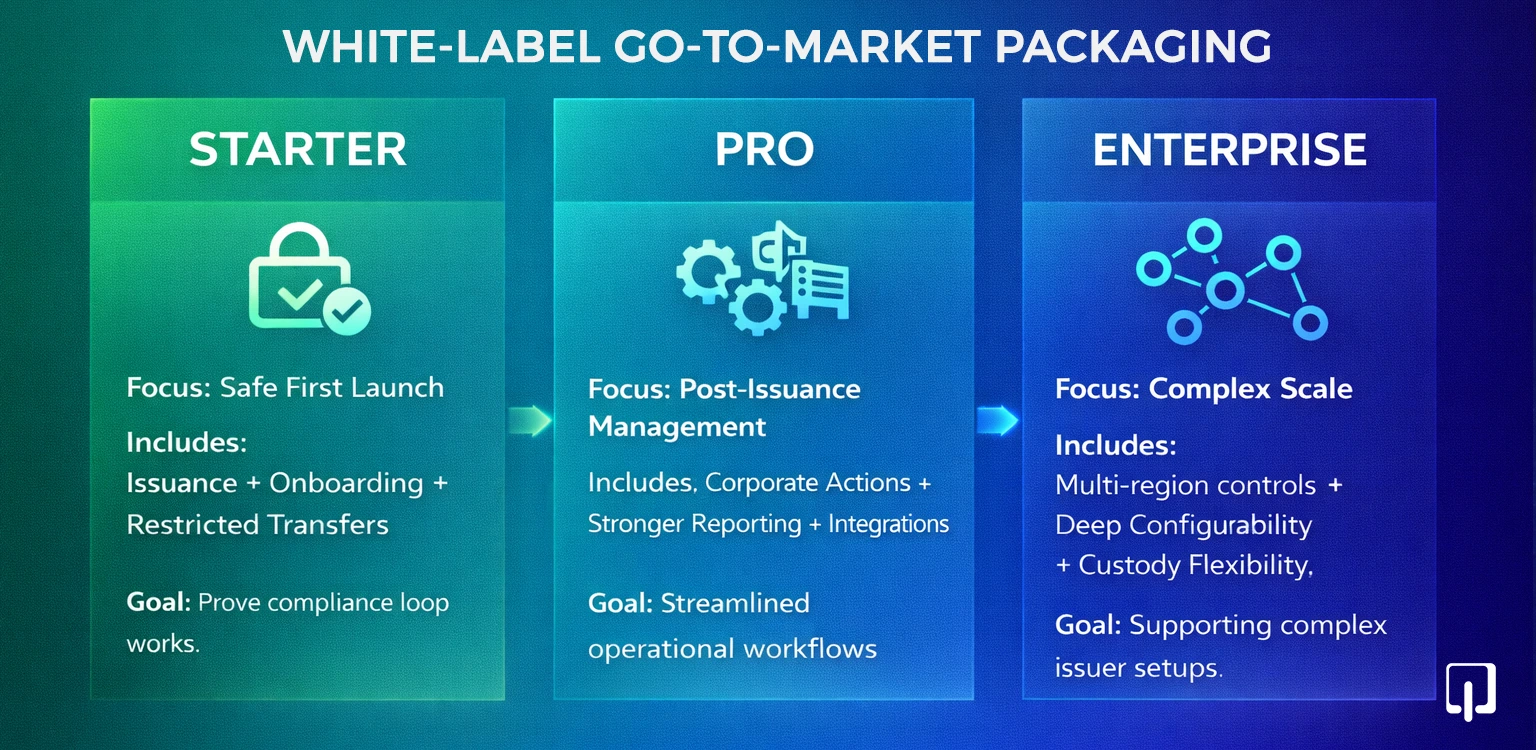
Packaging works best when it matches how issuers buy: they want a safe first launch, then expand capability once operations are stable. Tiers should be presented as maturity steps and as a feature bundle.
Starter: issuance + onboarding + restricted transfer, designed to prove the compliance and control loop works end-to-end.
Pro: adds corporate actions, stronger reporting, and integrations so assets can be managed after issuance with streamlined workflows.
Enterprise: adds multi-region policy controls, deeper configurability, and custody flexibility for complex issuer setups.
The strongest message is repeatability. Buyers care about custom development and about whether the platform launches new assets through configuration while staying controlled. That is what makes white-label different from a one-off build.
Even strong teams encounter the same failure points. These issues slow delivery, create compliance gaps, operational risk, and issuer distrust.
This is why successful development requires treating compliance, isolation, and governance as core architecture and implementation details.
A production-ready white-label RWA tokenization platform is configurable without fragility, compliant by design, auditable at any time, secure in both code and governance, and capable of supporting multiple issuers without rewriting core logic.
Building such a platform is about speed, correctness, durability, and long-term operation in real financial environments.
Copyright © 2026 Webmob Software Solutions